Overview
Cloud Security Posture Management (CSPM) is the process of securing multi-cloud environments through enhanced visibility, risk and misconfiguration identification, posture assessment, and compliance protocols. CodeAnt AI continuously monitor cloud infrastructure—such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS)—for gaps in security policy enforcement.Key Features
- Multi-Cloud Support: Currently supports AWS, GCP and Azure.
- Seamless Integration: Connect seamlessly with any cloud provider and continuously monitor for security vulnerabilities, misconfigurations, and compliance issues.
Setup
-
Permissions
-
Create a dedicated service account in each project
-
Grant the minimum roles
-
Viewer — lets the scanner read basic project metadata
-
Cloud Asset Viewer — needed for asset inventory reads
-
Service-agent prep — grab the project-number and service-agent address
-
Service Networking Service Agent — lets the Cloud Asset service do its job
-
Storage Object Admin (for the Cloud Asset service agent) — so exported dumps can land in GCS
-
Storage Admin (for your CSPM service account) — needed to create / clean up buckets
-
Service Usage Consumer — allows the scanner to call enabled APIs
cloudasset.assets.exportResourceandcloudasset.assets.exportIamPolicypermissions the scanner needs. -
Viewer — lets the scanner read basic project metadata
-
Enable the Cloud Asset Inventory API
-
Generate & download a JSON key
-
Create a dedicated service account in each project
-
Settings
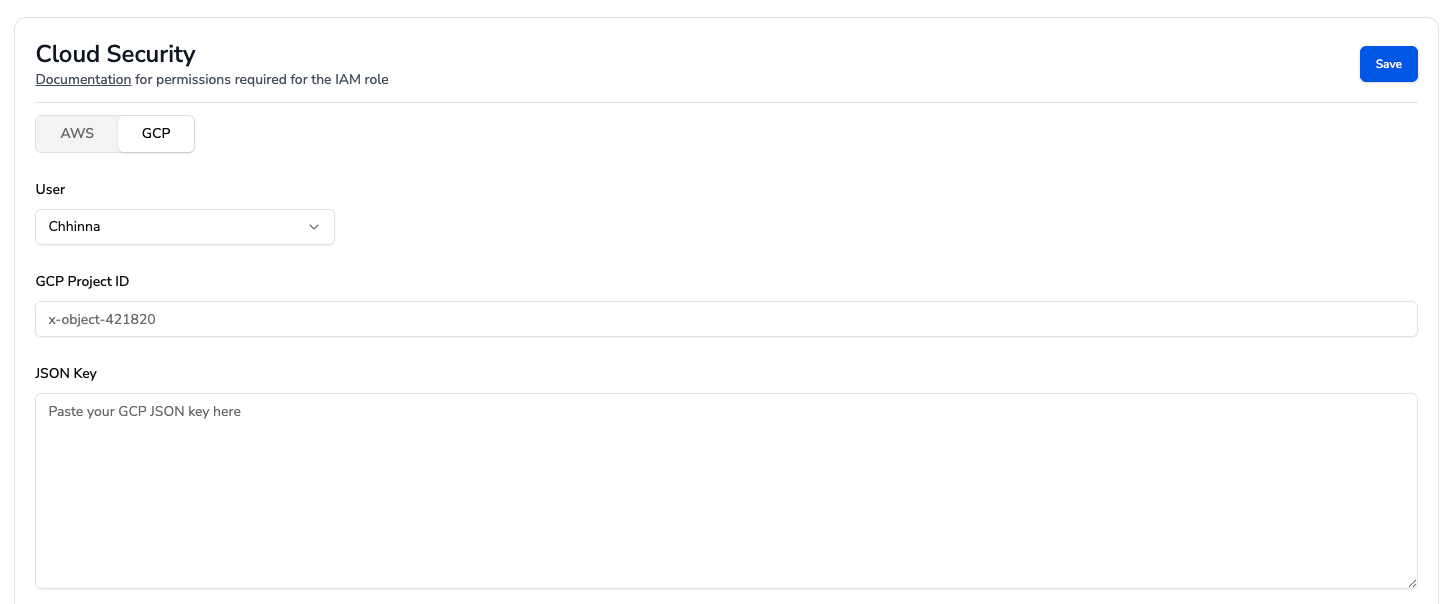
- In the CodeAnt UI navigate to Settings -> Cloud Security Settings -> GCP.
- Write project id, paste the JSON key and hit save.
-
-
Start a Scan
- Go to Cloud Security -> Start a New Scan and pick your GCP connection.
- Within 15-20 minutes, the scan will be completed, and you will see the results.