Overview
Cloud Security Posture Management (CSPM) is the process of securing multi-cloud environments through enhanced visibility, risk and misconfiguration identification, posture assessment, and compliance protocols. CodeAnt AI continuously monitor cloud infrastructure—such as Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS)—for gaps in security policy enforcement.Key Features
- Multi-Cloud Support: Currently supports AWS, GCP and Azure.
- Seamless Integration: Connect seamlessly with any cloud provider and continuously monitor for security vulnerabilities, misconfigurations, and compliance issues.
How It Works
- Permissions:
- An IAM role is needed with the required AWS managed permission roles.
- “ReadOnlyAccess” permission and a custom permission with following policy is required.
-
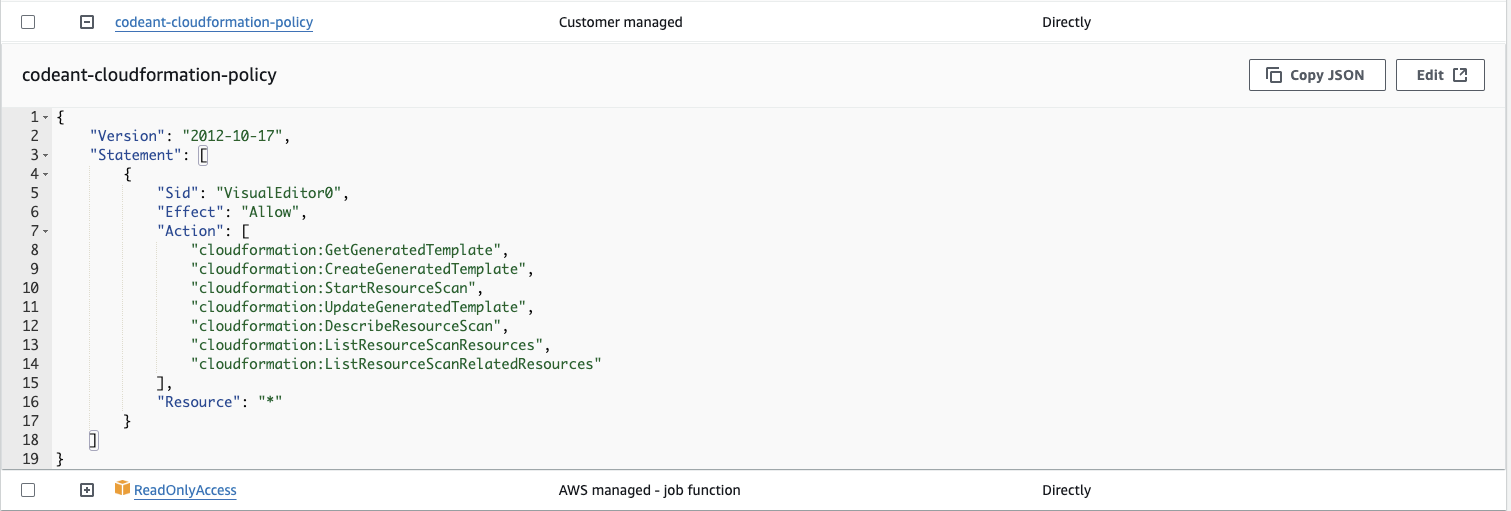
-
Settings:
- Once you have the access key and secret key, navigate to
Settings -> Cloud Security Settings. - Enter the credentials and save.
-
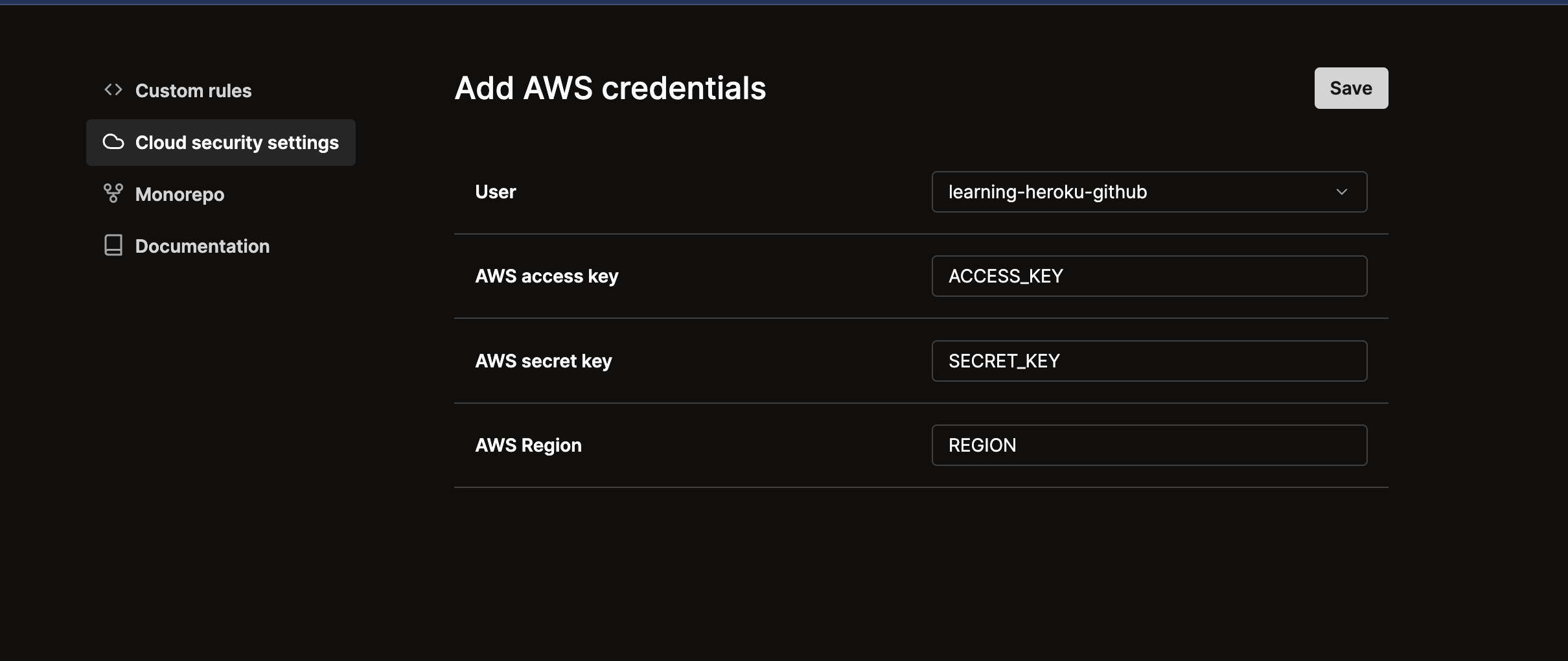
- Once you have the access key and secret key, navigate to
-
Start a Scan:
- Go to
Cloud Security -> Start a New Scan. - Within 15-20 minutes, the scan will be completed, and you will see the results.
- Go to
Benefits
- Enhanced Visibility: Gain complete visibility into your cloud infrastructure’s security posture.
- Risk and Misconfiguration Identification: Continuously identify and address risks and misconfigurations.
- Compliance Assurance: Ensure your cloud infrastructure complies with industry standards and protocols.